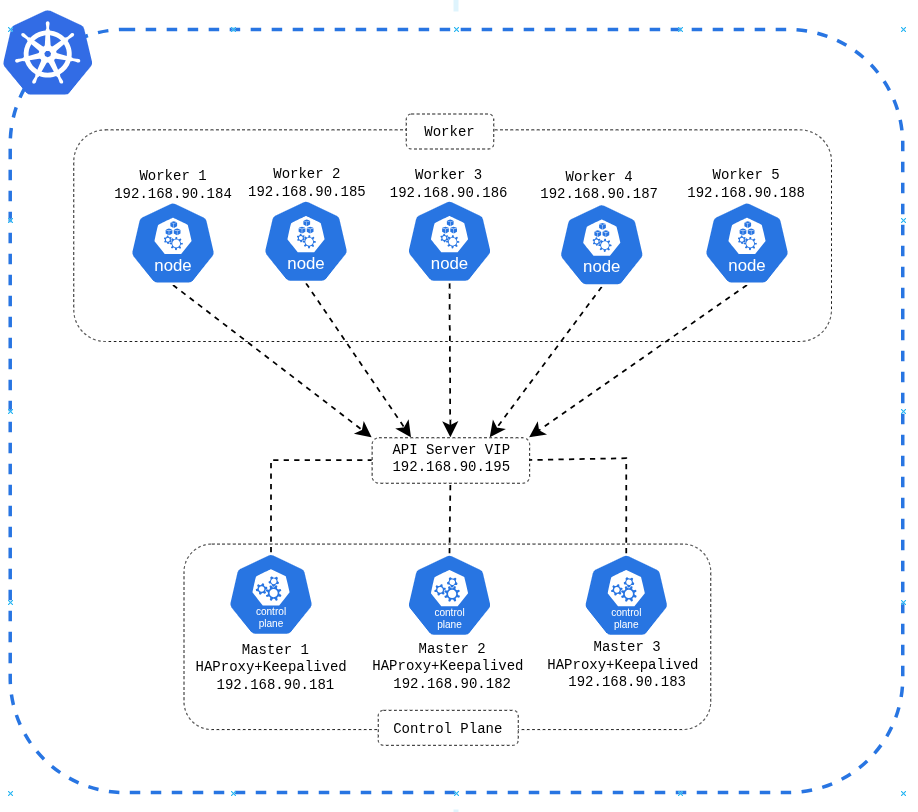
Update dan upgrade package pada setiap master dan worker
sudo apt update
sudo apt upgrade -yInstall dan konfigurasi keepalived pada setiap master
sudo apt install keepalived -yKonfigurasi keepalived.conf master 1
global_defs {
router_id ha_multi_master
vrrp_skip_check_adv_addr
vrrp_garp_interval 0.1
vrrp_gna_interval 0.1
enable_script_security
script_user root
}
vrrp_script chk_haproxy {
script "/usr/bin/killall -0 haproxy"
interval 2
weight 2
timeout 2
fall 2
rise 2
}
vrrp_instance LB1 {
state BACKUP
interface eth0
virtual_router_id 51
priority 103
advert_int 1
preempt_delay 180
accept
garp_master_refresh 5
garp_master_refresh_repeat 1
authentication {
auth_type P45S
auth_pass S3cR3T
}
unicast_src_ip 192.168.90.181
unicast_peer {
192.168.90.182
192.168.90.183
}
virtual_ipaddress {
192.168.90.195/24 dev eth0
}
track_script {
chk_haproxy
}
}Konfigurasi keepalived.conf master 2
global_defs {
router_id ha_multi_master
vrrp_skip_check_adv_addr
vrrp_garp_interval 0.1
vrrp_gna_interval 0.1
enable_script_security
script_user root
}
vrrp_script chk_haproxy {
script "/usr/bin/killall -0 haproxy"
interval 2
weight 2
timeout 2
fall 2
rise 2
}
vrrp_instance LB2 {
state BACKUP
interface eth0
virtual_router_id 51
priority 102
advert_int 1
accept
garp_master_refresh 5
garp_master_refresh_repeat 1
authentication {
auth_type P45S
auth_pass S3cR3T
}
unicast_src_ip 192.168.90.182
unicast_peer {
192.168.90.181
192.168.90.183
}
virtual_ipaddress {
192.168.90.195/24 dev eth0
}
track_script {
chk_haproxy
}
}Konfigurasi keepalived.conf master 3
global_defs {
router_id ha_multi_master
vrrp_skip_check_adv_addr
vrrp_garp_interval 0.1
vrrp_gna_interval 0.1
enable_script_security
script_user root
}
vrrp_script chk_haproxy {
script "/usr/bin/killall -0 haproxy"
interval 2
weight 2
timeout 2
fall 2
rise 2
}
vrrp_instance LB3 {
state BACKUP
interface eth0
virtual_router_id 51
priority 101
advert_int 1
accept
garp_master_refresh 5
garp_master_refresh_repeat 1
authentication {
auth_type P45S
auth_pass S3cR3T
}
unicast_src_ip 192.168.90.183
unicast_peer {
192.168.90.181
192.168.90.182
}
virtual_ipaddress {
192.168.90.195/24 dev eth0
}
track_script {
chk_haproxy
}
}Enable dan start keepalived service pada setiap master
sudo systemctl enable keepalived
sudo systemctl start keepalived
sudo systemctl status keepalivedInstall dan konfigurasi haproxy pada setiap master
sudo add-apt-repository ppa:vbernat/haproxy-3.0 -y
sudo apt update
sudo apt install -y haproxyKonfigurasi haproxy.cfg pada setiap master
global
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
stats socket /run/haproxy/admin.sock mode 660 level admin expose-fd listeners
stats timeout 30s
user haproxy
group haproxy
daemon
maxconn 5000
# Default SSL material locations
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
# See: https://ssl-config.mozilla.org/#server=haproxy&server-version=2.0.3&config=intermediate
ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options ssl-min-ver TLSv1.2 no-tls-tickets
defaults
log global
mode http
option httplog
option dontlognull
timeout connect 10s
timeout client 600s
timeout server 600s
timeout http-request 600s
errorfile 400 /etc/haproxy/errors/400.http
errorfile 403 /etc/haproxy/errors/403.http
errorfile 408 /etc/haproxy/errors/408.http
errorfile 500 /etc/haproxy/errors/500.http
errorfile 502 /etc/haproxy/errors/502.http
errorfile 503 /etc/haproxy/errors/503.http
errorfile 504 /etc/haproxy/errors/504.http
listen stats
bind *:8000
mode http
stats enable
stats uri /stats
stats refresh 15s
stats hide-version
stats show-legends
stats admin if TRUE
stats realm Haproxy\ Statistics
stats auth admin:BlMkV90PjBrM26!
listen k8s
bind *:8443
mode tcp
balance roundrobin
option tcplog
option tcp-check
server master1 192.168.90.181:6443 check inter 5s fall 3 rise 2
server master2 192.168.90.182:6443 check inter 5s fall 3 rise 2
server master3 192.168.90.183:6443 check inter 5s fall 3 rise 2
Cek konfigurasi dan restart haproxy service
sudo haproxy -c -f /etc/haproxy/haproxy.cfg
sudo systemctl restart haproxy
sudo systemctl status haproxyInstall dan konfigurasi kubernetes
Enable IPv4 packet forwarding pada setiap master dan worker
cat <<EOF | sudo tee /etc/sysctl.d/k8s.conf
net.ipv4.ip_forward = 1
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
EOF
sudo sysctl --systemEnable overlay dan br_netfilter module pada setiap master dan worker
cat <<EOF | sudo tee /etc/modules-load.d/k8s.conf
overlay
br_netfilter
EOF
sudo modprobe overlay
sudo modprobe br_netfilterDisable swap pada setiap master dan worker
sudo swapoff -a
sudo sed -i -E 's/^([^#].*?\s+swap\s+sw\s+.*)$/# \1/' /etc/fstabSet up docker apt repository pada setiap master dan worker
sudo apt install ca-certificates curl
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
sudo tee /etc/apt/sources.list.d/docker.sources <<EOF
Types: deb
URIs: https://download.docker.com/linux/ubuntu
Suites: $(. /etc/os-release && echo "${UBUNTU_CODENAME:-$VERSION_CODENAME}")
Components: stable
Signed-By: /etc/apt/keyrings/docker.asc
EOFSet up kubernetes apt repository pada setiap master dan worker
sudo apt install -y apt-transport-https ca-certificates curl gnupg
curl -fsSL https://pkgs.k8s.io/core:/stable:/v1.35/deb/Release.key | sudo gpg --dearmor -o /etc/apt/keyrings/kubernetes-apt-keyring.gpg
sudo chmod 644 /etc/apt/keyrings/kubernetes-apt-keyring.gpg
echo 'deb [signed-by=/etc/apt/keyrings/kubernetes-apt-keyring.gpg] https://pkgs.k8s.io/core:/stable:/v1.35/deb/ /' | sudo tee /etc/apt/sources.list.d/kubernetes.list
sudo chmod 644 /etc/apt/sources.list.d/kubernetes.listInstall package yang dibutuhkan untuk kubernetes pada setiap master dan worker
sudo apt update
sudo apt install -y kubeadm kubectl kubelet containerd.io net-toolsHold kubeadm, kubectl, dan kubelete agar tidak auto update pada setiap master dan worker
sudo apt-mark hold kubeadm kubectl kubeletGenerate default config untuk containerd pada setiap master dan worker
sudo containerd config default | sudo tee /etc/containerd/config.toml > /dev/nullEnable systemdcgroup pada setiap master dan worker
sudo sed -i -E 's/^(\s*)SystemdCgroup = false/\1SystemdCgroup = true/' /etc/containerd/config.toml
sudo systemctl restart containerd
sudo systemctl status containerdInit kubernetes cluster, jalankan hanya pada master 1
sudo kubeadm init --pod-network-cidr=10.6.0.0/16 --control-plane-endpoint=192.168.90.195:8443 --apiserver-advertise-address=192.168.90.181 --upload-certsOutput hasil dari init cluster kubernetes (perhatikan tulisan yang diwarnai)
Your Kubernetes control-plane has initialized successfully!
To start using your cluster, you need to run the following as a regular user:
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
Alternatively, if you are the root user, you can run:
export KUBECONFIG=/etc/kubernetes/admin.conf
You should now deploy a pod network to the cluster.
Run "kubectl apply -f [podnetwork].yaml" with one of the options listed at:
https://kubernetes.io/docs/concepts/cluster-administration/addons/
You can now join any number of control-plane nodes running the following command on each as root:
kubeadm join 192.168.90.195:8443 --token 41acnb.00g7xbgains1y33u \
--discovery-token-ca-cert-hash sha256:9422778ec7af68c7c4028298c09345fe5d0d487cd51d7b45073837375e02a4a7 \
--control-plane --certificate-key e8ddd99bb9d577f3f1159f333d54169f62772ee755b3e1c67e1976fc621fc1bf
Please note that the certificate-key gives access to cluster sensitive data, keep it secret!
As a safeguard, uploaded-certs will be deleted in two hours; If necessary, you can use
"kubeadm init phase upload-certs --upload-certs" to reload certs afterward.
Then you can join any number of worker nodes by running the following on each as root:
kubeadm join 192.168.90.195:8443 --token 41acnb.00g7xbgains1y33u \
--discovery-token-ca-cert-hash sha256:9422778ec7af68c7c4028298c09345fe5d0d487cd51d7b45073837375e02a4a7Konfigurasi penggunaan kubernetes cluster, jalankan hanya pada master 1 sebagai user biasa
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/configSebagai alternatif konfigurasi penggunaan kubernetes cluster, jalankan hanya pada master 1 sebagai user root
export KUBECONFIG=/etc/kubernetes/admin.confInstall addons untuk networking dan network policy, jalankan hanya pada master 1
kubectl apply -f https://raw.githubusercontent.com/projectcalico/calico/v3.31.3/manifests/calico.yamlJoin master ke cluster kubernetes, jalankan pada master lainnya selain master 1 dan sebagai user root
kubeadm join 192.168.90.195:8443 --token 41acnb.00g7xbgains1y33u \
--discovery-token-ca-cert-hash sha256:9422778ec7af68c7c4028298c09345fe5d0d487cd51d7b45073837375e02a4a7 \
--control-plane --certificate-key e8ddd99bb9d577f3f1159f333d54169f62772ee755b3e1c67e1976fc621fc1bfKonfigurasi penggunaan kubernetes cluster, jalankan hanya pada master lainnya, selain master 1 sebagai user biasa
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/configSebagai alternatif konfigurasi penggunaan kubernetes cluster, jalankan hanya pada master lainnya, selain master 1 sebagai user root
export KUBECONFIG=/etc/kubernetes/admin.confJoin worker ke cluster kubernetes, jalankan di semua worker sebagai user root
kubeadm join 192.168.90.195:8443 --token 41acnb.00g7xbgains1y33u \
--discovery-token-ca-cert-hash sha256:9422778ec7af68c7c4028298c09345fe5d0d487cd51d7b45073837375e02a4a7Pengecekan status node pada cluster kubernetes, jalankan disalah satu master (rekomendasi pada master 1)
kubectl get node -o wide